19 Apr Internet Service Provider Support for Distributed Denial of Service (DDoS) Mitigation
Distributed denial of service (DDoS) is a formidable cybersecurity risk threating companies, organizations, and government departments. Enterprises typically subscribe to anti-DDoS attack service providers since the volume of traffic from such attacks can be far beyond the capacity of the network under attack. However, the effectiveness of the anti-DDoS service is dependent on the Internet service provider (ISP) connectivity. In this article, the mechanism of DDoS and the role of ISPs to mitigate it are discussed.
What is distributed denial of service?
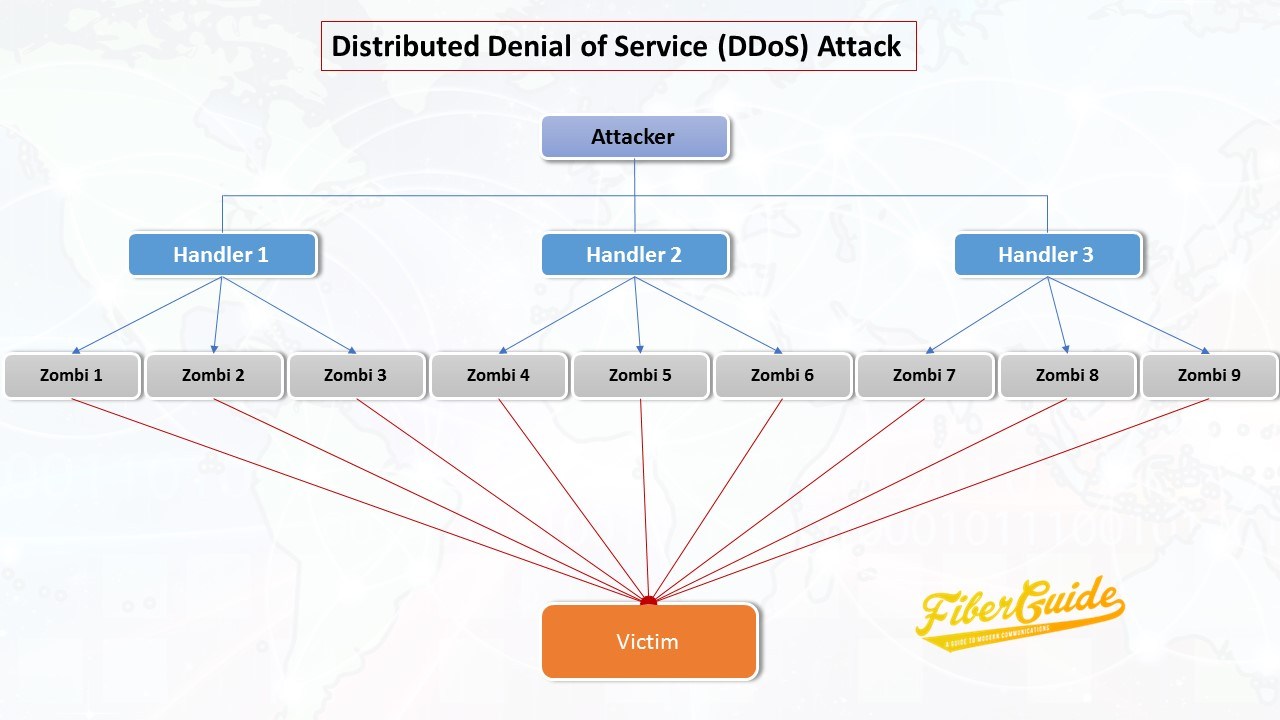
A distributed denial of service attack is an attempt to deny service to legitimate network users by inundating a target server with a high volume of bogus network traffic. In most cases, the bogus traffic originates from a network of malware infested Internet connected devices known as botnets. The “distributed” comes from the fact that multiple Internet connected devices, usually from geographically dispersed locations, are utilized.
Such attacks are becoming more prevalent and the volume of the attack traffic is increasing – thanks to the rapidly growing number of unsecured Internet connected devices that can be used as botnets.
The most notable recent attack was in October 2016 and it targeted Dyn, a domain name server (DNS) provider. The DNS translates domain names of the form fiberguide.net to its numeric IP equivalency of the form 107.180.48.31 that can be understood by web servers. The attack was accomplished by continuously making a huge number of bogus domain name lookup requests from tens of millions of IP addresses, making it virtually impossible for bona fide web servers to get their domain name lookup requests resolved. Consequently, many online platforms in Europe and North America became inaccessible.
A large number of Internet connected devices including printers, home routers, cameras, computers and baby monitors were first infected with the Mirai virus and then turned into a huge botnet. An estimated 1TBps of traffic was generated between the botnet and the dyne servers, making this the worst DDoS attack ever. It is feared that with the proliferation of Internet of things (IoT), the worst is yet to come.
The relentless DDoS onslaught on networks is getting exacerbated by the easiness of setting up and initiating such attacks. Any Tom and Dick with a little bit of money can arrange for a DDoS attack and wreak havoc on targeted web servers. Unscrupulous business competitors, anti-government activists (or hacktivists), extortionists and “script kiddies” targeting video game servers have been known to pay third parties for the infrastructure and software to attack target networks. They typically rent the use of botnets from so-called herders who control multitudes of compromised Internet connected devices.
DDoS Mitigation and the role of the ISP
The most commonly used effective approach to DDoS mitigation consists of two main components – detection and filtering of Internet traffic to remove the bogus data. While some enterprises place their entire DDoS mitigation tools on their networks, the emerging trend is to use a hybrid approach. In a hybrid approach, a detection appliance is placed on the premises while a filtering or “scrubbing” of the traffic is outsourced on the cloud. When the on-premise system detects an attack, Internet traffic is redirected to the scrubbing center where bogus traffic is filtered out and genuine traffic is redirected to the end user network.
Your Internet service provider (ISP) can play a pivotal role in the DDoS mitigation process which should be taken in consideration when selecting an ISP. In addition to connecting you to the Internet and other networks, your ISP provides important functions in support of your DDoS strategy:
- It diverts your compromised Internet traffic to an anti-DDoS or scrubbing center using the lowest latency route.
- It provides adequate bandwidth required to forward large volumes of traffic to the scrubbing center. Only a few enterprises have the capacity to single handedly absorb the large amounts of traffic volumes commensurate with today’s DDoS attacks.
The following are some of the important criteria to consider when selecting an ISP for anti-DDoS support:
The ISP should be the upstream provider for your anti-DDoS scrubbing center.
By using your ISP as the upstream provider for your anti-DDoS scrubbing center, the number of hops required to deliver the clean traffic and latency can be managed more effectively.
The ISP should have multiple routing plans
The route used to redirect compromised traffic and to deliver clean traffic can have a profound impact on the quality of the final traffic and the cost of the process. A plan can be chosen based on your most important requirements at any given time. If cost is the most important factor, then the most cost efficient route can be used. On the other hand, if latency is a major factor, then the shortest route will be preferred. As an example, some anti-DDoS center upstream providers in China will route traffic to Ch必利勁
inese or Hong Kong scrubbing centers through the USA – the least cost route. For latency sensitive traffic, routing can be done directly within China.
For more information or recommendations on ISPs supporting anti-DDoS, please leave a comment or contact Fiberguide.


Sorry, the comment form is closed at this time.